Information, Product, and Cyber Security
Basic Concept
The Olympus Group recognizes that information, product, and cyber security (hereinafter referred to as “information security”) risks not only have a direct impact on our business but also pose serious risks to our customers—namely, medical institutions—as well as to the healthcare system itself. In addition, the proper management of information security risks and incident response are becoming increasingly important for ensuring our company’s sustainable growth and enhancing the competitive advantage of our products and services. At the same time, we believe that countermeasures against information security risks should not be limited to departments with specialized expertise in this field but must instead be addressed at the company-wide level, involving all related functions and departments. Furthermore, we consider it essential to actively communicate and collaborate with our customers in the medical field, business partners, industry associations, and government agencies.
From the perspective of corporate risk management, we visualize risks based on a unified global standard across the entire Group and implement risk management measures across all related functions. Moreover, through the execution of a comprehensive and harmonized new governance model and strategy, we are particularly focused on achieving the following:
- Enhancing cyber-attack resilience not only in our general IT systems but also in our products, services, and their development and manufacturing environments
- Ensuring continuous product security across the entire product lifecycle, including the supply chain, to maintain stable delivery of products and services
- Identifying sensitive information across the organization and establishing mechanisms to ensure its safe and effective use
Information Security Governance
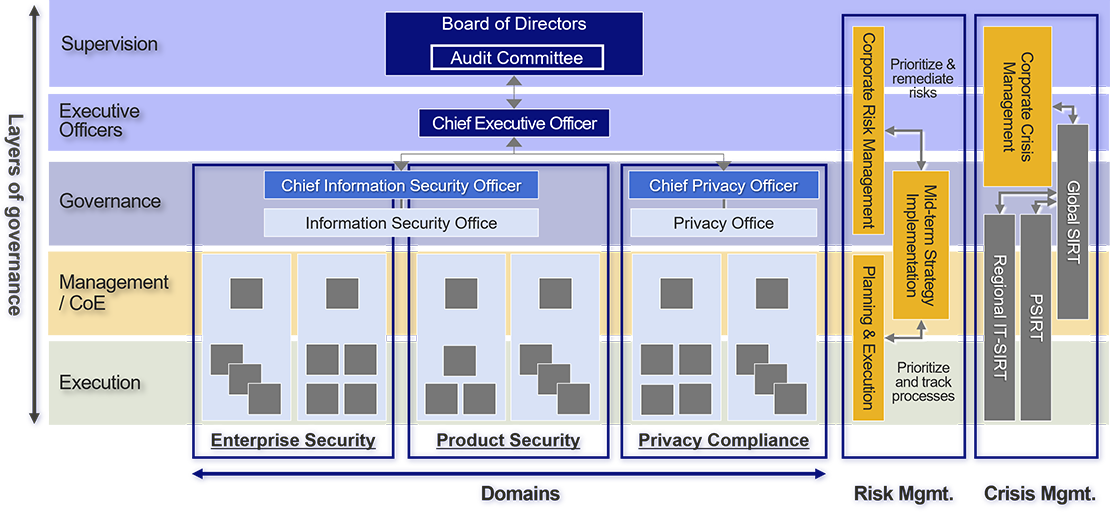
In accordance with our corporate governance structure for overall management, Olympus has established an information security governance structure consisting of an executive function, led by the Chief Executive Officer (CEO) and the Board of Directors (BoD), which oversees the executive function.
As part of the executive function, the Global GRC Head is accountable to the BoD and external stakeholders for matters related to information security. The responsibility for execution lies with the Chief Information Security Officer (CISO) and their dedicated organization. They oversee the formulation and implementation of Group-wide strategies and risk management related to information security.
Regarding the supervisory function, the BoD holds ultimate oversight responsibility as part of corporate governance for overall management. In particular, the Audit Committee plays a key role in supervising the execution of duties by executive officers and others as part of its auditing responsibilities. The Global GRC Head and the CISO, as part of the executive function, regularly report to the BoD on the overall information security status of the Olympus Group and report promptly when there are changes in the environment. They also report to the Audit Committee more frequently on a regular basis.
As part of our information security promotion framework, we have introduced a three-line defense model with the aim of achieving balanced security measures in accordance with risk levels. This framework consists of: a governance layer that oversees the development and execution of Group-wide information security strategies; control towers in each function and department that develop and manage implementation plans based on those strategies; and an execution layer responsible for the actual implementation within each function and department.
The security control functions are organized into three defined domains, each with responsibility for execution in their respective areas of expertise: Enterprise Security (including information security for general IT systems and operational technology systems), Product Security (information security of our products and services), and Data Governance.
Regarding risk management, the CISO and their dedicated organization conduct Group-wide risk assessments, considering various external factors such as trends in cyber-attacks and industry best practices. Based on these assessments, medium-term strategies are formulated by considering our business strategies, customer requirements, and trends in laws and regulations. Based on the formulated strategies, each function and department is achieving a balanced risk mitigation across the Group based on a unified standard.
In the event of an information security incident, especially a cyber-attack, it is essential to have a crisis management system that enables prompt and appropriate management decisions in collaboration with the entire Group and relevant organizations. To this end, we have established the Global SIRT, PSIRT, and Regional SIRTs as our crisis management structure and conduct regular training.
Number of Information Security Incidents and Breaches*1
In recent years, ransomware and supply chain attacks have surged, and the healthcare industry has become one of the primary targets. Vulnerabilities in general IT systems, operational technology systems, and products have been exploited, heightening the risk of system outages and threats to patient safety.
The table below presents the number of global incidents reported across the Olympus Group over the past three years.
Based on the governance model, we strive to prevent the occurrence of such incidents. If they do occur, we respond swiftly to minimize their impact. We also analyze the root causes of each incident and use the insights gained to improve our risk assessments and strengthen preventive measures. Furthermore, through continuous training, we are working to build a more resilient security framework.
| Item | FY2023 | FY2024 | FY2025 |
|---|---|---|---|
| Number of information security breaches or other cybersecurity incidents | 4 | 2 | 2 |
Related Information
*1 The figures in the table are based on the standards on display in GRI 418-1 (2016).

